One of the most dangerous aspects looming the computer world is security threats. It is estimated that around three trillion dollars are lost in cyber crimes every year. This figure is expected to double by 2021. With all of these threats lurking around, it is difficult to track and eliminate every threat, especially as the number of users is rising exponentially.
The most popular among the existing cyber threats now is the distributed denial of service (DDoS) attack. DDoS attacks have adversely affected businesses on a large scale.
Now, with machine learning prevailing in the tech ecosystem, eliminating DDoS attacks has found a new way.
Session Initiation Protocol (SIP) And Voice Over Internet Protocol (VoIP)
With the growing number of digital devices and the abundant availability of the internet, VoIP is the preferred method for voice and multimedia communications.
In order to establish a VoIP session, Session Initiation Protocol (SIP) is the popular means of initiating and these sessions. A simple version of the SIP/VoIP architecture is given below:
- User Agent (UA): The active entities in the session which represent the endpoints of SIP. For example, in the context of voice communications, the caller and the receiver, which denote the endpoints in the session.
- SIP Proxy Server: An intermediate entity which acts as a client and a server simultaneously during the session. The role of this server is to maintain send and receive requests as well as transfer information to and fro from the users.
- Registrar: This component takes care of authentication and register requests for the UA.
All of the SIP communication is logged by the VoIP provider. This is important because it gives out billing and accounting information for service providers based on users’ activity. Interestingly, it can also give out information regarding intrusion or suspicious activity present in the network. This can be a breeding ground for DDoS attacks if left neglected.
Aggregating ML Techniques In VoIP
The researchers consider the same SIP VoIP architecture and use five standard ML classifier algorithms in their experiments, which are as follows:
- Sequential minimal optimisation
- Naive Bayes
- Neural networks
- Decision trees
- Random Forest
These algorithms are set up for dealing with communications directly in the experiment. Then, classification features are generated once the network is made anonymous using keyed-hash method authentication code (HMAC) for the VoIP communications. The algorithms are tested under 15 DDoS attack scenarios. In order to do this, a ‘test bed’ of DDoS simulations is designed by the researchers which is shown below:
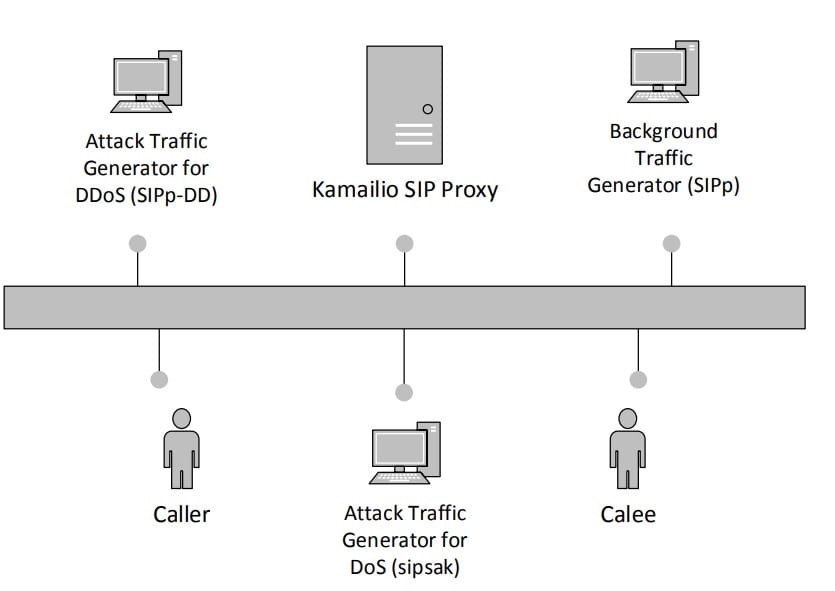
“Three or four different Virtual Machines (VMs) have been used for the SIP proxy, the legitimate users, and the generation of the attack traffic depending on the scenario. All VMs run on an i7 processor 2.2 GHz machine having 6GB of RAM. For the SIP proxy, we employed the widely known VoIP server Kamailio (kam, 2014). We simulated distinct patterns for both legitimate and DoS attack traffic using sipp v.3.21 and sipsak2 tools respectively. Furthermore, for the simulation of DDoS attack, the SIPp-DD tool has been used. The well-known Weka tool has been employed for ML analysis.”
Training and Testing process for algorithms include both normal traffic and attack traffic. To simulate the attack traffic, they use a range of random high call rates to give a feel of real VoIP whereas the normal traffic has normal, observed call rates.
The training scenario in the experiment is denoted as SN1 and testing scenarios are denoted as SN1.1, SN1.2, SN1.3 etc. A detailed description is given here.